The adoption rate of phishing-resistant forms of multi-factor authentication (MFA) such as WebAuthn hardware keys, device-based passkeys and Okta’s own FastPass nearly doubled in 2023, a study of Okta workplace users finds. But their overall usage rate is still very small.
At the same time, the adoption rate of all forms of MFA, weak or strong, seems to be flattening out at about 65%, despite recent government and private-industry mandates.
The silver lining is that phishing-resistant forms of authentication are demonstrably easier to use than passwords, which may lead organizations and consumers alike to abandon passwords sooner than expected.
“It took a little time to convince the world of the virtues of multi-factor authentication (MFA),” says Okta CEO and co-founder Todd McKinnon in the introduction to the company’s 2024 Secure Sign-in Trends Report.
“We expect the next wave of MFA adoption won’t be driven by security purists,” he adds. “It’s going to be driven by a demand for a better user experience and higher security assurance. Once you’ve experienced passwordless, whether as an employee or a customer, you will never want to go back.”
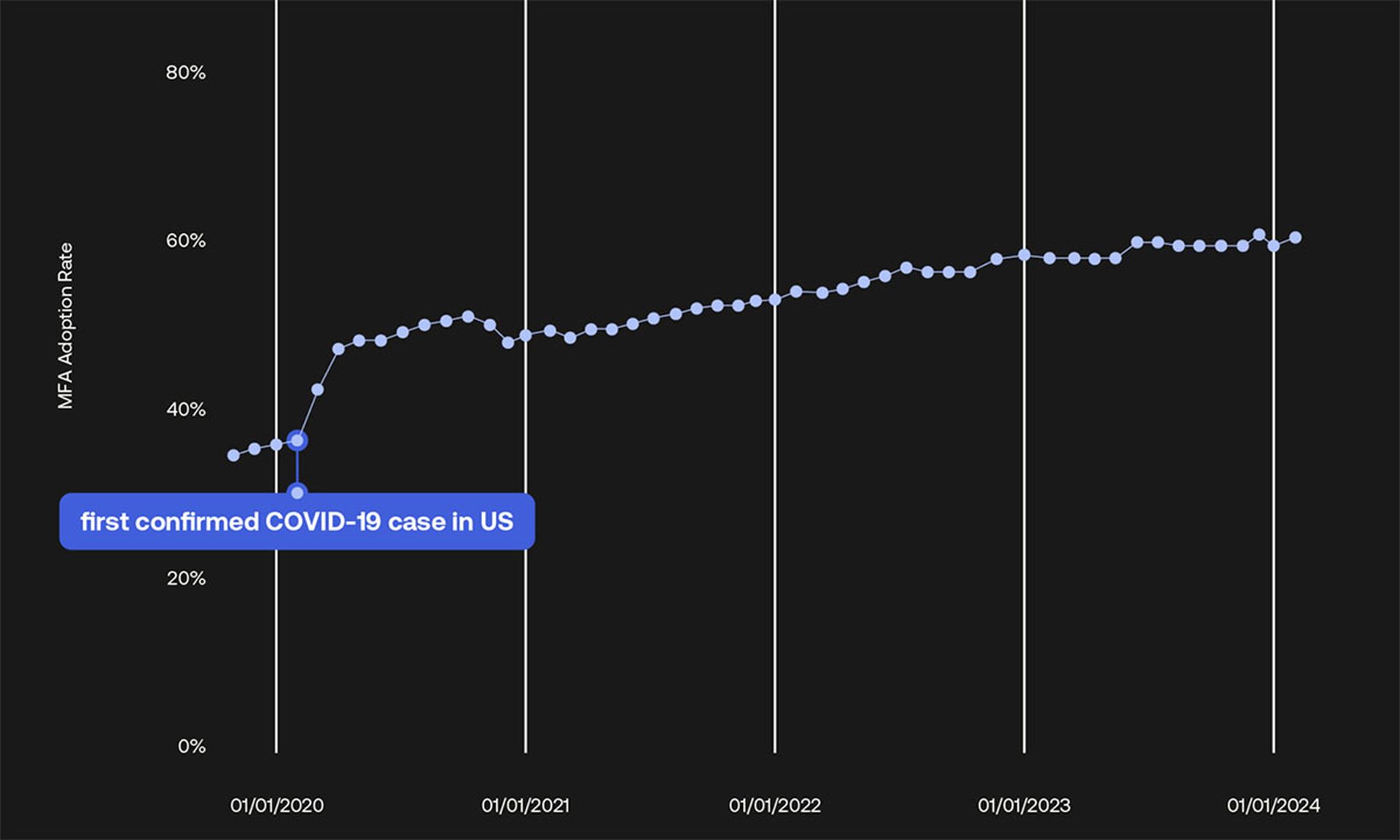
MFA usage overall is high, but may be tapering off
Taking individual user behavior among organizations that have deployed Okta Workforce Identity Cloud as the survey base, the report finds that adoption of any form of MFA, which had slowly inched up to about 35% by the beginning of 2020, greatly accelerated during the COVID-19 pandemic, quickly rising to 50%.
“During the pandemic, MFA adoption went mainstream,” McKinnon observes. “Okta observed a 15% rise in the use of MFA within a few short months, as the world rushed to support remote work.”
The adoption rate rose steadily during 2021 and 2022 to about 65% but was nearly flat in 2023. This is despite recent mandates by the U.S. federal government that government agencies and contractors implement MFA, and similar initiatives by private companies, including Google and Okta itself, which now requires that administrators of Okta Workforce Identity Cloud use MFA for their own accounts. (Ninety-one percent of Okta administrators used MFA by the end of 2023.)
MFA adoption rates vary widely by industry, the report finds. The technology sector led the way at 88% at the beginning of 2024, while the warehousing and transportation sector brought up the rear at 38%. Government adoption was 55%, up from 48% at the beginning of 2023, but the sector was nevertheless only three notches up from the bottom.
Interestingly, the Okta survey finds “a rough inverse correlation between the number of employees and the rate of MFA adoption.”
Organizations with fewer than 300 staffers had an MFA adoption rate of at least 82%, while those with more than 20,000 people on staff averaged 59%. We’d have thought that bigger organizations would do better, as they do in most other aspects of cybersecurity.
Okta’s report notes that “large enterprises may be slow to adopt modern identity frameworks due to the complexity of replacing legacy infrastructure” and “are also more likely to use multiple identity providers and may use MFA solutions other than Okta.”
However, there’s little regional variation in MFA usage. At the beginning of 2024, MFA adoption rates were at 68% in Europe, the Middle East and Africa, 67% in North and South America, and 61% in Asia and the Pacific.
Okta’s research measures “user-level MFA use”, the report explains, or “the percentage of users who signed in using MFA over a given period.” That’s a more reliable metric than measuring how many client companies had implemented MFA as an option or how many users had enrolled in an MFA program.
The survey also measures only MFA events in Okta Workforce Identity Cloud. Some clients, the report notes, may have MFA “provided by other identity providers and make use of enterprise federation or social login to connect to Okta.”
In terms of what kind of MFA is most often used, it shouldn’t be a surprise that 95% of Okta Workforce Identity Cloud users still include passwords as part of their MFA schemes. Most of us reading this story probably do as well.
We were a bit heartened, however, to see that push notifications were more frequently used than SMS-texted temporary codes as the second authentication factor, 29% to 17%. Close behind at 14% were “soft token” code-generating apps like Authy or Google Authenticator.
Although both push notifications and soft tokens can be phished, they’re still stronger than SMS texted codes. However, their rankings in this survey of Okta Workforce Identity Cloud users may not be indicative of usage in the wider world.
Phishing-resistant MFA is slowly growing
It’s often said that any form of MFA is better than no MFA at all. But that doesn’t take into account the false assurances that many users get when they enroll into an SMS-based or push-notification program.
Most users, especially on the consumer side, aren’t prepared to deal with smooth-talking criminals who sweet-talk them into revealing their Zelle account credentials, or who bombard them with push notifications until the users tap “yes” to make it stop.
That’s why phishing-resistant forms of MFA based on biometrics, public/private cryptographic key exchanges, embedded secure chips or a combination of any of these factors are so important. A phisher can’t cajole your passkey private key out of you, because you don’t know the key. Nor will a phishing site work, because the passkey or Okta FastPass won’t recognize the site as legitimate.
For the purposes of the 2024 Secure Sign-in Trends Report, Okta puts phishing-resistant forms of authentication into three categories.
Smart cards: These are similar to a modern ATM or charge card. There’s a computer chip embedded in one end, and you insert that end into a card reader.
Deploying smart cards can be expensive because each user needs both a card reader and a unique card that must be manufactured at a central location. Smart cards are common among banking customers in Europe, but in North America they often protect highly sensitive government or corporate assets.
WebAuthn/FIDO2-compliant protocols: These include hardware keys such as a Yubikey or Google Titan key, as well as the device-bound passkeys currently being used and promoted by Apple, Google and Microsoft.
Hardware keys work well and are very user-friendly. Google has distributed them to all its employees, but retail prices can range from $20 to $80 per unit.
Passkeys create a public/private key pair between the secure element on a Windows PC, Mac, iPhone, iPad or Android device with a specific online service. The user verifies their identity using facial or fingerprint recognition on a smartphone, tablet, or Mac, or Windows Hello on a PC.
Passkeys are cheap to implement and very safe when bound to individual devices. However, to appeal to consumers, Apple and Google have decided to make passkeys transferable to other devices (a feature Microsoft is also working on) which may run afoul of company security policies.
Okta FastPass: A more enterprise-friendly alternative to passkeys, this protocol also uses Windows Hello, fingerprint readers or facial recognition to verify the user, then exchanges public/private cryptographic keys to verify the device. It also used risk-based authentication to provide context to each login attempt.
Like passkeys, FastPass can be used to authenticate accounts without using a password, whether the account has a password associated or not. But FastPass gives administrators more managerial control than passkeys, and its side-channel communications can reveal failed phishing or brute-force attempts. As of this writing, passkeys have no such notification mechanism.
“Today, Okta FastPass is the only authenticator capable of creating server-side events when a phishing attempt results in a failed origin check,” the report notes. “When a phishing site domain name or cookie mismatch is detected, FastPass rejects the request and alerts the end user and administrators.”
Are we ready for a world without passwords?
Okta’s survey revealed that while 95% of Okta Workforce Identity Cloud users still relied on passwords for their MFA logins over the course of January 2024, 5% of users did not. The implication is that a phishing-resistant authenticator was used along with a weaker form of authentication, such as Okta FastPass’s combination of a smartphone fingerprint scan and a temporary code.
“For the first time, we can see clear progress in password eradication,” wrote McKinnon in a blog post accompanying the release of the 2024 Secure Sign-in Trends Report. “Almost 5% of users no longer use passwords in a month.”
Six percent of Okta Workforce Identity Cloud users employed Okta FastPass in 2024, as opposed to only 2% in 2023, the report found. Three percent used WebAuthn authenticators, up from 2%, although the 2024 rates are higher for privileged users.
“FIDO2 WebAuthn adoption among users with admin permissions grew from 8% to 9% over the past year, while the use of Okta FastPass among administrative users grew from 5% to 13%,” says the report.
The end goal for the identity industry is to eliminate passwords altogether. Like Microsoft, Okta is moving toward this by giving users the option of setting up accounts without any passwords at all by instead combining other forms of authentication.
“A passwordless world isn’t a sci-fi dream,” said McKinnon in his blog post. “It’s a reality that many Okta customers are living now.”
But can passwordless really catch on? Enterprise IT managers are resistant to passwordless implementation for reasons of cost and control. For their part, customers are just getting used to the weaker forms of MFA; going passwordless is indeed a sci-fi dream for many.
Yet Okta analyzed the various forms of authentication used in MFA, ranging from passwords to WebAuthn, and found that the phishing-resistant forms were among the most friction-free to use while providing the most security.
At an average of four seconds to use, they were 50% faster than typing in a password (six seconds) and three times as fast as typing in a one-time passcode (12 seconds).
“Security vs. user experience is a false choice,” the 2024 Secure Sign-in Trends Report states. “In our authenticator performance and usability assessment, FastPass and FIDO2 WebAuthn came out on top as more secure and user-friendly than other options, even under revised, more practical criteria.”
In a graphic plotting usability versus security along an X/Y axis, only FastPass and WebAuthn are in the “magic quadrant” above 0.50 on both axes.
Most of the options fall close to the 45% 1:1 line, with WebAuthn the furthest out on the line with more than 0.75 for both security and usability. FastPass has a perfect 1.00 for security but about 0.66 for usability. Passwords score below zero for security and about 0.4 for usability.
“We hope that once privileged users experience how easy it is to sign in with passwordless, phishing-resistant authenticators,” the report states, “we will see a broader acceleration in MFA adoption for all users.”
Steps to accelerate your organization’s MFA adoption rate
Even if your organization isn’t prepared for the passwordless future, Okta’s report recommends measures you can take to get you a little closer to it.
1. Require MFA for all users and require phishing-resistant MFA for those users who access sensitive information.
2. Convince the top brass that MFA deployment is a mission-critical priority. Show them examples of real-life breaches that could have been prevented by MFA.
3. Implement advanced IAM mechanisms such as least-privilege access, risk-based authentication and time-limited privileges.
4. Plot a path that leads to all users adopting phishing-resistant MFA.
5. Once all users have implemented phishing-resistant MFA, phase out the use of passwords entirely.