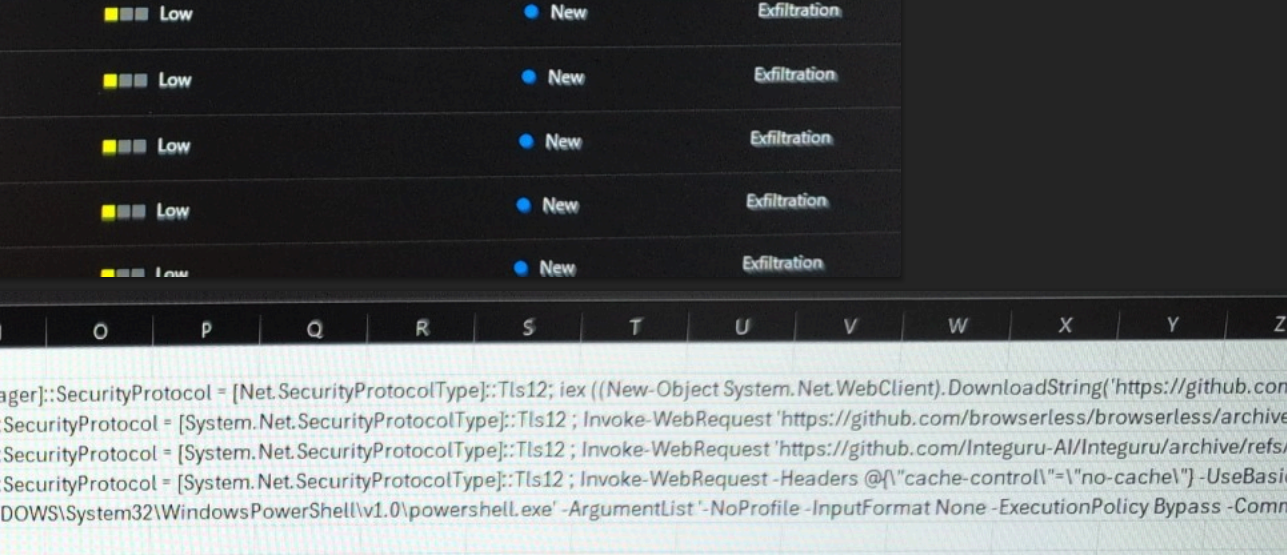
Can a three-year deadline in Armenia’s Civil Code derail a $331 million investment arbitration? The recent ICSID award in Rasia FZE and Joseph K. Borkowski v. Republic of Armenia says yes, exposing a critical spot in investor-state dispute settlement (ISDS): the quiet power of domestic law to strangle investment claims.
The dispute stemmed from a grand infrastructure project, a North-South railway corridor meant to link the Persian Gulf to the Black Sea via Armenia. In 2012, Armenia signed two Concession Agreements with Rasia FZE, a Dubai-based investment vehicle, to conduct feasibility studies and project development. The Claimants asserted Armenia subsequently: (1) abruptly withdrew political backing; (2) failed to provide promised support; and (3) engaged with competing investors, actions they claimed constituted both contractual breaches and violations of the US–Armenia BIT’s FET guarantees. Joseph K. Borkowski, Rasia’s US-national CEO, joined the arbitration seeking $331 million for the project’s collapse.