Securing A Converged IoT-IIoT Future – Go Health Pro
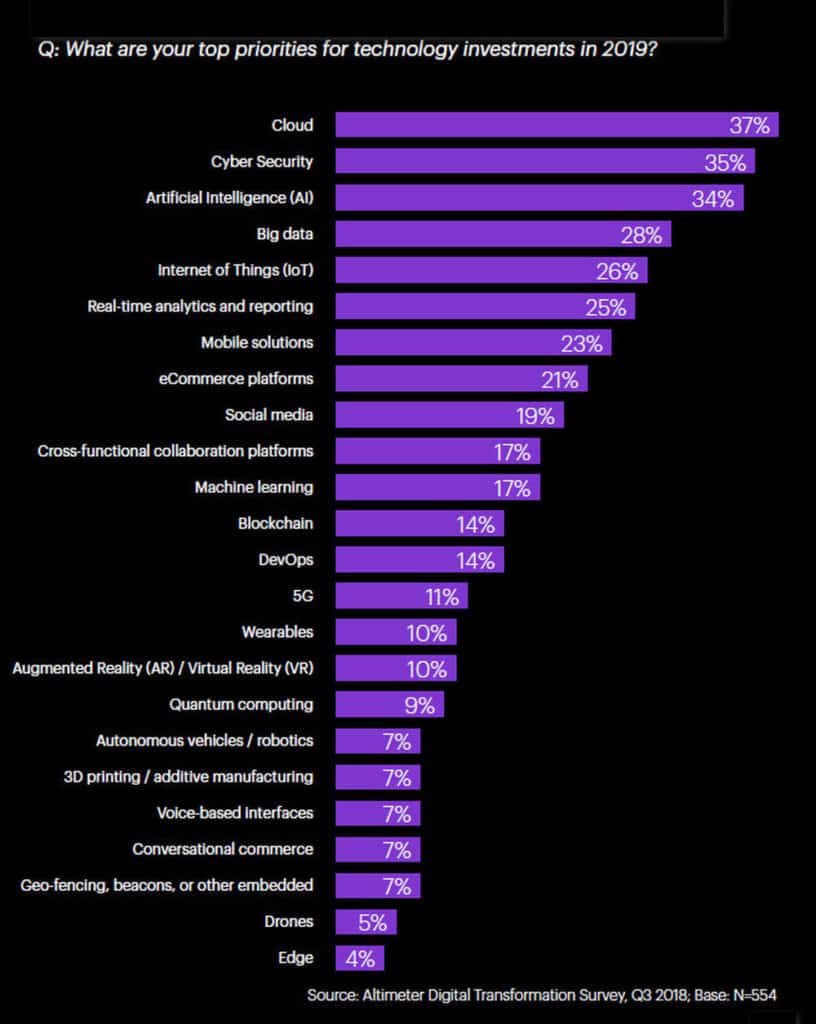
The Altimeter report, 2018-2019 State of Digital Transformation, reveals that business growth remains the primary driver of digital transformation initiatives. But while market pressures like business opportunities (51%) and increased competitive pressure (41%) are high on the agenda of the C-suite, high-profile data breaches and new regulatory standards like GDPR are also providing impetus to … Read more